实验目标
掌握IP欺骗的原理
实验环境
实验机环境:debian10(GNU/Linux)
实验原理
Scapy的是一个强大的交互式数据包处理程序。它能够伪造或者解码大量的网络协议数据包,能够发送、捕捉、匹配请求和回复包等等
学习过程中我参考的这份scapy教程
实验步骤
-
安装scapy并启动
安装:
sudo apt-get install scapy启动:
scapy
-
查看空的ip包,并设置目标ip地址
>>> ip Traceback (most recent call last): File "<console>", line 1, in <module> NameError: name 'ip' is not defined >>> IP() <IP |> >>> target="192.168.3.75" >>> ip=IP(dst=target) >>> ip <IP dst=192.168.3.75 |>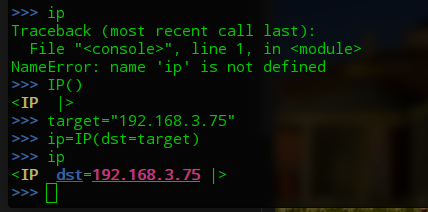
-
设置TTL
>>> ip.ttl=32 >>> ip <IP ttl=32 dst=192.168.3.75 |>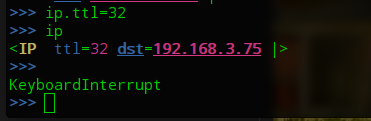
-
设置源IP地址,不设置则为真实的IP地址,在这里设置为伪造的IP地址
>>> ip.src="192.168.100" >>> ip.src '192.168.100' >>> ip <IP ttl=32 src=192.168.100 dst=192.168.3.75 |>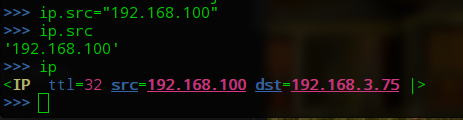
-
查看数据包
>>> hexdump(ip) 0000 4500001400010000200015EAC0A80064 E....... ......d 0010 C0A8034B ...K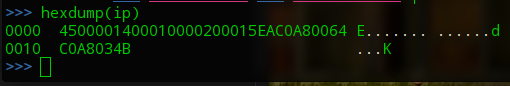
-
发送数据包
>>> send(ip) . Sent 1 packets.
-
也可以嵌套其他协议,如TCP、Ether。嵌套之后使用默认值。同样可以发送
>>> hexdump(Ether()/ip) 0000 7C67A2A01243E0B9A51A30A408004500 |g...C....0...E. 0010 001400010000200012EAC0A80364C0A8 ...... ......d.. 0020 034B .K >>> send(Ether()/ip) WARNING: Mac address to reach destination not found. Using broadcast. . Sent 1 packets.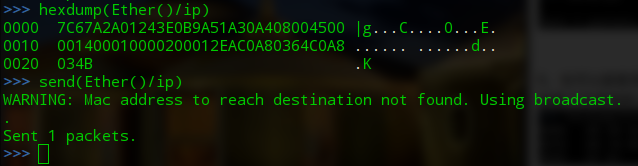
使用scapy实现其他类型欺骗
-
增加MAC地址欺骗
>>> mac=Ether() >>> mac <Ether |> >>> mac.src="66:fa:c7:85:7e:19" >>> mac.dst="66:fa:c7:85:7e:10" >>> mac <Ether dst=66:fa:c7:85:7e:10 src=66:fa:c7:85:7e:19 |> >>> hexdump(mac/ip) 0000 66FAC7857E1066FAC7857E1908004500 f...~.f...~...E. 0010 001400010000200012EAC0A80364C0A8 ...... ......d.. 0020 034B .K >>> send(mac/ip) WARNING: Mac address to reach destination not found. Using broadcast. . Sent 1 packets.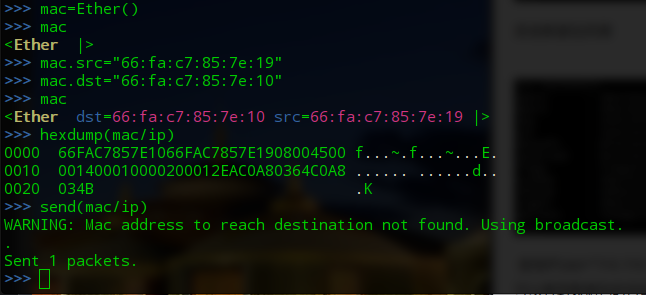
-
增加TCP端口欺骗
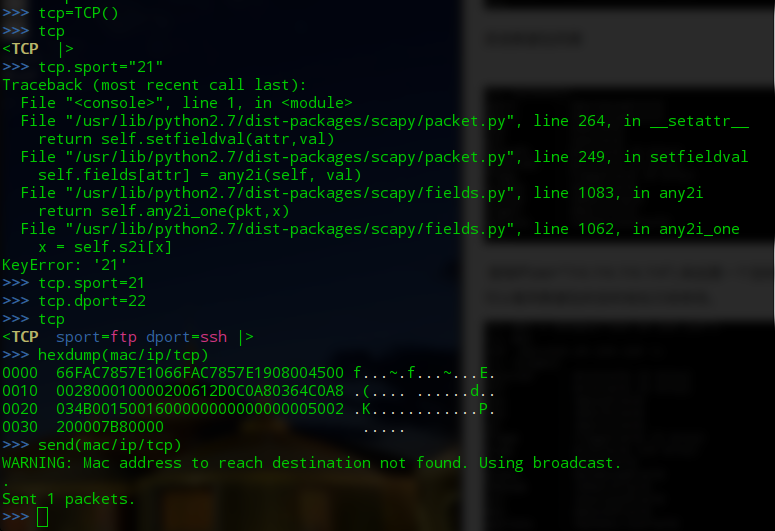
>>> tcp=TCP() >>> tcp <TCP |> >>> tcp.sport=21 >>> tcp.dport=22 >>> tcp <TCP sport=ftp dport=ssh |> >>> hexdump(mac/ip/tcp) 0000 66FAC7857E1066FAC7857E1908004500 f...~.f...~...E. 0010 002800010000200612D0C0A80364C0A8 .(.... ......d.. 0020 034B0015001600000000000000005002 .K............P. 0030 200007B80000 ..... >>> send(mac/ip/tcp) WARNING: Mac address to reach destination not found. Using broadcast. . Sent 1 packets.